coScene Data Security White Paper

We are well aware of the high importance you and your company place on data
security, which is the core consideration when designing our products, services, and features. At coScene, we
always prioritize data and privacy protection in our work.
Our security architecture is built on a series of rigorous control measures. Our
cyber security and access control policies are carefully designed to strictly follow the principle of least
privilege, ensuring that only authorized users can access necessary resources. Our data transmission and storage
procedures use advanced encryption technology to ensure the security of data in static and transmission states.
By using temporary keys and customer master keys supported by hardware security modules (HSMs),
we further strengthen the protection of metadata and configuration data for data transmission and long-term
storage.
In addition, we have implemented monitoring and anomaly detection mechanisms
based on audit logs, which not only enable our team to identify and respond to potential security threats in
real time and proactively, but also provide your company with detailed historical records when conducting
critical activities such as threat and risk assessment and access audit.
We have forward-looking planning and deployment for the security and compliance
of our business. Our systems respect and comply with the laws and regulations where the data is located,
ensuring that business and sensitive data do not cross the geographical location of their physical storage media
without the affirmative consent of users.
As a leading data platform, we are committed to providing secure, transparent,
and data-driven decision support. This article aims to elaborate on a series of security measures taken by the
coScene platform, in order to demonstrate our commitment to the security and reliability of data
storage.
From the beginning, the design of coScene was to provide a very high level of
security protection for its products and users. We make extensive use of established mature standards and
protocols in the industry to ensure our first-class product security and permission control.
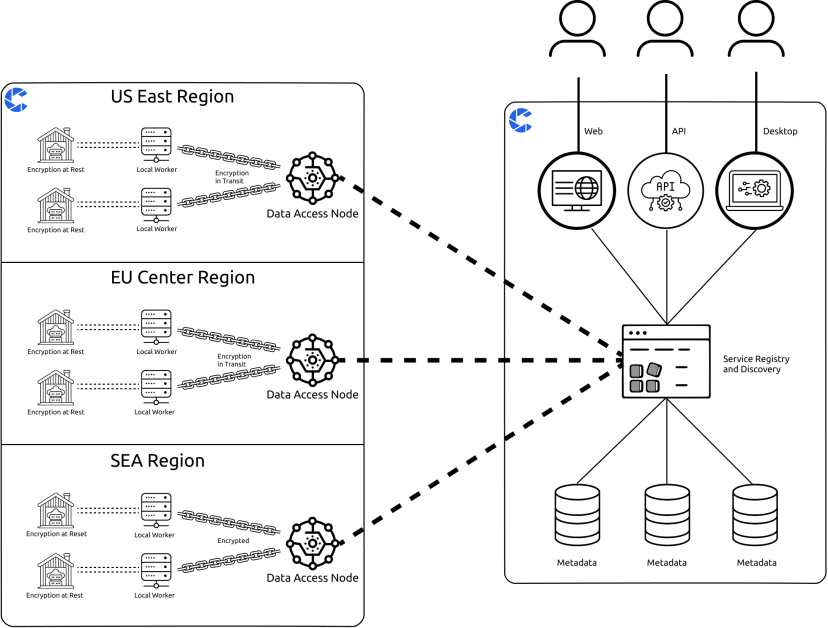
Data security during transmission (Data in
Transit)
At coScene, data link security is the cornerstone of our core security features.
We are committed to ensuring the security and integrity of user data during transmission. We deeply understand
that every aspect of data transmission is crucial, whether it is the connection between users and coScene
services or the communication between internal services of coScene, we ensure its security and
reliability.
Encryption and Authentication: We implement advanced encryption measures for every connection, using protocols
such as TLS 1.2, SSH-2, and IPSec to provide an impregnable security barrier for data transmission. These
protocols not only ensure the security of data during transmission, but also ensure the integrity of
data.
Digital Certificates: With Level 2 CA Certificates issued by DigiCert , the world's
leading provider of enterprise digital certificates, we ensure that our connections are authenticated and
encrypted to international standards, providing our customers with the highest standards of
security.
Continuous evaluation: Our professional team regularly evaluates and reviews the connections used to
ensure that the encryption algorithms and key verification methods selected always comply with current best
security practices.
Security Monitoring and Response: We implement continuous security monitoring of critical tools we rely on, such
as OpenSSL. Once known vulnerabilities are discovered, we are able to respond quickly, deploy necessary security
patches, and ensure that our software and systems remain at the forefront of industry security
standards.
Through these comprehensive measures, coScene promises to provide users with a
secure and reliable data transmission environment. Our goal is to protect customer data from unauthorized access
and destruction, ensuring data security and business continuity.
Static -state data storage security (Data at
Rest)
User metadata and structured data
In the coScene platform, we give the highest priority to data protection work
generated by users during use. This includes but is not limited to sensitive data such as user configuration
details, transaction information, audit records, etc. For example, customized event fields, user events,
recorded raw information, and activity logs are strictly managed according to the needs of each organization. We
ensure that users can export and delete data completely according to their needs at any time, thus ensuring that
users have complete control over their own data.
The coScene platform has implemented end-to-end encryption measures for all data
stored by users. This measure ensures that even in extreme cases, such as hackers bypassing access restrictions
and directly obtaining data on storage media, these data will become unreadable ciphertext due to encryption.
Without the corresponding key, these data cannot be utilized, and the key itself is strictly protected in the
memory of the data service.
The coScene platform performs static encryption processing on all stored data.
This means that the encryption process has been completed locally before the data is uploaded to the coScene
platform. All files uploaded to the platform are encrypted locally before being securely transmitted to the
object storage. This practice effectively prevents the risk of data leakage that may occur when data is
illegally accessed or destroyed in the object storage. For more information about coScene's static data
encryption process, please refer to our "
coScene Data Security Solution
".
coScene provides users with a complete Data Warehousing isolation solution and
data location selection to meet the needs of users and their enterprises in data compliance, review, and
localization. We not only provide current data storage options, but also plan future expansion plans to ensure
coverage of a wider range of geographic locations and compliance requirements. coScene's current and planned
data warehousing location options include but are not limited to the following regions:
|
Area
|
Area
|
Alibaba Cloud Ali Cloud Aliyun
|
Azure
|
AWS
|
|
Chinese mainland
|
Shanghai
|
Has supported
|
In the plan
|
Not applicable
|
|
|
Hangzhou
|
Has supported
|
Not applicable
|
Not applicable
|
|
|
Beijing
|
In the plan
|
In the plan
|
In the plan
|
|
|
Ningxia
|
Not applicable
|
Not applicable
|
In the plan
|
|
North America
|
Virginia - East US
|
Not applicable
|
Has supported
|
In the plan
|
|
|
Oregon - West US
|
Not applicable
|
Has supported
|
In the plan
|
|
|
California - West US
|
Not applicable
|
Has supported
|
In the plan
|
|
Europe
|
Netherlands
|
Not applicable
|
In the plan
|
In the plan
|
|
|
Germany
|
Not applicable
|
In the plan
|
In the plan
|
Completely transparent logs and behavior
records
coScene is committed to providing industry-leading regulatory standards and
transparency levels. We enable users to easily monitor and review system activities by providing a range of
user-friendly tools. These tools include but are not limited to:
•
Transaction-level log : Record the details of each transaction to ensure the traceability of
transactions.
•
User Behavior Tracking : Monitor every step a user takes on the platform to increase
transparency.
•
Event operation record : Detailed record of the operation history of all events for easy problem
tracking and analysis.
•
Data operation record : Record every operation on the data to ensure the integrity and consistency of
the data.
All of this information can be directly disclosed to user administrators through
the coScene platform, ensuring visibility and transparency of operations, thereby enhancing users' trust in the
platform.
For customers with higher k security requirements, coScene further provides
operation log services similar to cloud providers. This not only meets customers' high standards in compliance,
supervision and security assurance, but also demonstrates our deep understanding and commitment to customers'
security needs.
Through these advanced logging services, customers can gain deeper insights into
system activity to stay ahead in complex security environments.
Three-party and single sign-on
coScene platform currently supports login through two widely used third-party
services, DingTalk and Feishu , which not only brings convenience to users, but also ensures the security of the
login process. In addition, we also provide a one-time password login method based on email to meet the needs of
different users.
We are committed to continuously expanding and enriching our login options. In
the future, we plan to integrate more third-party login vendors to provide more diverse login methods. At the
same time, we are also actively promoting the integration work that supports single sign-on (SSO) methods such
as SAML, and expect to meet with users in the near future.
We encourage users to adopt single sign-on, which not only simplifies the login
process and improves User Experience, but also reduces the use of passwords and reduces security risks caused by
password leakage, thereby improving the security and reliability of the entire system.
The coScene platform has built a powerful role-based access control system
(RBAC), which gives administrators precise control over internal personnel accessing specific resources at
multiple levels such as organization, warehouse, and project. This system design aims to meet the complex
requirements of data access management for enterprises of different scales and needs.
Our system provides a series of predefined standard role templates, allowing
users to quickly perform initial configuration, saving time and reducing configuration errors. These templates
cover common responsibilities and permission requirements, bringing users the convenience of Plug and Play
(plug-and-play).
More importantly, the RBAC system of coScene allows organizational
administrators to customize settings based on these standard templates. This means that users can fine-tune the
permissions of characters according to their specific needs, achieving more precise access control.
In order to help users better utilize this system, our product documentation
includes detailed instructions and guidelines on role-based access control. By reading these materials, users
can gain a deeper understanding of how to configure and optimize their access control policies to ensure the
security and compliance of enterprise resources.
Audit log anonymization and intelligent
monitoring
coScene platform performs anonymization on users' audit logs to protect their
privacy and data security. At the same time, we use advanced pattern detection technology to conduct in-depth
analysis of logs to identify potential data risks and abnormal behaviors.
Real-time alarm and security response
Once suspicious behavior such as a large number of non-allowlisted network
segments or downloads outside of commonly used network segments is detected, our system will immediately trigger
an alarm mechanism that matches the Cloud as a Service provider level and service level. This ensures that users
can receive notifications about potential security threats in the first place.
Internal security review
While notifying users, coScene's internal security review team will quickly
intervene to conduct a detailed review of suspicious behavior. Our expert team will use their professional
knowledge and technical means to ensure security from the program to the operational level, while maximizing the
risk of human error and external intrusion.
coScene platform has taken comprehensive and strict measures to ensure data
security and privacy, which provide users with a secure and transparent data environment while complying with
the requirements of the General Data Protection Regulation (GDPR).
Customer Data means any information, including Personal Data, copied,
transmitted, or generated by our customers and their end users through our services.
Customers are the owners and controllers of customer data, and coScene is the
data processor. During the customer's use of coScene services, the customer retains ownership and control of the
data in their account.
System and software specifications
At the system software level, coScene helps customers maintain control over
privacy and data security in various ways.
1.
Data Encryption: We encrypt all data links and storage to ensure that it is
fully protected, whether in transmission or storage. By using advanced encryption technology, we ensure that
data cannot be accessed without authorization at any time.
2.
Data Minimization: coScene strictly adheres to the principle of data
minimization, collecting and storing only necessary information and avoiding processing any personally
identifiable information ( PII ). This practice reduces the risk of data leakage while ensuring the efficiency
of our services.
3.
Access Control: We have implemented strict access control mechanisms to ensure
that only authorized users can access sensitive data in the system. This permission-based control system ensures
data security while also supporting compliance requirements.
4.
Data masking and pseudonymization: We implement different levels of masking or
pseudonymization on data displayed by different users and systems to protect sensitive data from unauthorized
access.
5.
Logging and monitoring: coScene provides a comprehensive logging and monitoring
system to track and record user operations and system events in real time, in order to conduct security audits
and timely discover potential security threats.
6.
Data erasability and portability: We support complete erasability and
portability of data, allowing users to delete all information they have in our systems or transfer data to other
service providers when needed.
7.
Privacy settings and display notifications: coScene provides clear privacy
settings and notifications, allowing users to fully understand how their data is collected, processed, and
protected. This transparency not only helps users use our services with confidence, but also enhances their
trust in us.
In addition to careful consideration in system design, we have also established
a series of strict processes and systems aimed at minimizing the impact of individual factors on system
functions and decisions within the organization. The following are our main measures:
1.
Privacy impact assessment before feature launch: Before any new feature goes
live, we conduct a detailed privacy impact assessment to identify and mitigate potential impacts on user
privacy. This assessment process involves XFN collaboration to ensure potential privacy risks are considered
from multiple perspectives and appropriate measures are taken to prevent data leakage and abuse.
2.
Data Retention Policy: coScene formulates and strictly implements data retention
and deletion policies in accordance with legal requirements and business needs. For example, for users who no
longer use the product, we have clear data retention policies to ensure that user data is deleted after a
certain period of time, thereby reducing the risks that long-term data storage may bring.
3.
Accident Response Plan: We have a comprehensive accident response mechanism to
deal with data breaches and other security incidents. This includes recovery and compensation from the initial
stage of the accident to the later stage. Our goal is to control losses as soon as possible, restore normal
operations, and provide necessary compensation and support to affected users according to the
situation.
4.
Third-party audits: coScene regularly invites external security experts and
audit teams to conduct third-party security audits. These independent assessments help us identify potential
security bugs and compliance risks, ensuring that our security measures and compliance are always in the best
state.
5.
Employee training: We provide regular data security and privacy protection
training to our employees to increase their awareness of the importance of data protection and ensure that they
understand the latest security practices and company policies. This training not only includes basic data
processing guidelines, but also covers how to identify and prevent potential security threats.
coScene's efforts in GDPR compliance and data security demonstrate our boundless
passion for safeguarding customer data. By combining advanced system security measures (such as comprehensive
data encryption and strict access control) with meticulous organizational policies (including employee training,
privacy assessments, and third-party audits), we are committed to meeting or even exceeding GDPR standards at
all levels. The dual approach of system software and human resources management not only strengthens the
internal team's emphasis on data security, but also ensures the strong protection of our system. coScene's goal
is to provide users with a secure and reliable data environment, ensuring that every user's data receives the
most comprehensive and advanced protection, and becoming a practitioner of data security and privacy protection
in the industry.
Analysis of the possible impact of data
breaches
If the permissions of the data warehouse storing user
data are leaked, for example, in Hybrid Cloud mode, local data warehouse permissions are
leaked
•
In the engraved line, all data stored in the data warehouse is strictly
encrypted and hashed, so even if the permissions of the data warehouse are leaked, it will not directly lead to
the readability of the data. The time required to brute force crack the AES256 encryption algorithm far exceeds
the time that the earth has existed, so the security of these encrypted data is extremely reliable (Note
1).
If the data of the execution database is
engraved
•
In terms of user information and privacy data, coScene relies on the leading
DingTalk and Feishu login systems in China, so we do not store any information that can be traced back to the
user's specific identity. Even if coScene servers are attacked, malicious intruders can only obtain
non-sensitive information, such as random User Identification, recorded metadata, event metadata, etc. They
cannot directly obtain sensitive data stored in the data warehouse from coScene servers.
If the intruder obtains both the execution database of
the engraved line and the data of the data warehouse at the same time
•
coScene uses the Cloud as a Service key management service selected by the user
(such as Alibaba Cloud Ali Cloud Aliyun's KMS) to encrypt data. Therefore, even if the data of the data
warehouse and coScene execution database are leaked, without the corresponding key, intruders still cannot
decrypt and view user data.
The intruder also obtained the execution database of
the engraved line, the data of the data warehouse , and the key of the Cloud as a Service vendor
KMS
•
In this extreme case, coScene relies on the key management service provided by
Cloud as a Service vendor to periodically (set to N days) update the keys. Therefore, in the case of a
complete leak, at most, only N days of data encrypted with this key will be exposed. coScene will
re-encrypt and store the affected data after the leak is repaired to ensure data security.
1.
Brute force cracking AES256:
https://scrambox.com/article/brute-force-aes/
2.
Alibaba Cloud Ali Cloud Aliyun KMS:
https://www.aliyun.com/product/kms
3.
Data Security Solution:
https://coscene0.feishu.cn/wiki/wikcnPkxIAkhoAADeB2Etp4ugre